Aircrack-ng is a set of tools for auditing wireless networks. The interface is standard and some command use skills will be required in order to operate this application. Key new features include: Better documentation and support. More cards/drivers supported. More OS and platforms supported. WEP dictionary attack. Fragmentation attack. Hacking a WPA/WPA2 WiFi Network Using Mac OS X -aircrack-ng. Hacking a WPA/WPA2 WiFi Network Using Mac OS X -aircrack-ng.
Introduction to Aircrack-ng Suite of Tools
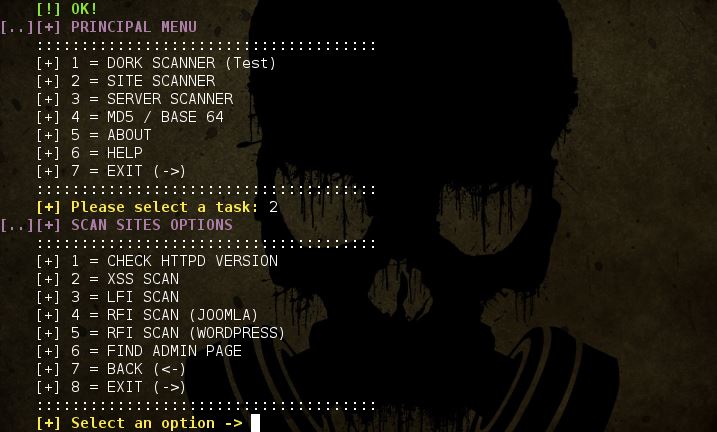
Hello friends,
This is the First part of Chapter 3 from the “Rootsh3ll WiFi Security and Pentesting Series”. In case you missed the series you can start following here.
In Chapter 2, We will cover:
- Introduction to Aircrack-ng Suite of tools
- Introduction to Wireshark
- WEP cracking using Aircrack-ng
- WPA/WPA2 Personal cracking using Aircrack-ng
- WPS cracking
As every topic above is crucial to understand, This chapter will have a dedicated post on each topic. Hence, the first part(out of 5) will cover the “Introduction to Aircrack-ng Suite of tools“
[YB]This article is an excerpt from my WiFi Penetration testing andSecurity eBook for aspiring WiFi hackers and Wireless security enthusiasts. Click here to learn more[/YB]
Lets begin!
When we begin and expertise in wireless hacking, some helpful tools are always with the Hacker, Aircrack-ng suite of tools
What is Aircrack-ng ?
Aircrack-ng is a suite of tools use by beginners and experts for Wireless sniffing, cracking and creating rogue AP’s.
Conventional definition goes like :
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured
Aircrack-ng suite include tools like:
- Airmon-ng
- Airodump-ng
- Airbase-ng
- Aireplay-ng
- Airolib-ng
- Aircrack-ng
- and lots more
We will discuss about the tools above, as they are most frequently used tools and used in almost every Wireless Pentest.
Aircrack-ng comes for Linux, Mac, and Windows and comes pre-installed in Kali Linux. We can manually install Aircrack-ng on Linux, Mac or Windows.
Download Aircrack-ng
Latest version of Aircrack-ng can be downloaded from its official site, Aircrack-ng.org
For Linux and Mac, it can be installed from source code, and
For Windows, Aircrack-ng provides pre-compiled binaries. You can download the zip here
Install Aircrack-ng
In Windows, Aircrack-ng comes in a download-and-execute pre-compiled binary package.
Installing on Windows:
- Unzip aircrack-ng*.zip (aircrack-ng-1.2-rc2-win.zip, as latest version)
- Start using
Here is complete tutorial on installing on windows
There are 2 ways of installing Aircrack-ng in Linux:
- Using terminal
- Using source-code
We will take an example of
Installing Aircrack-ng on Ubuntu
From Terminal:
apt-get is the package installer in Ubuntu.
different distributions have different package installers.
example,
For Red Hat: yum
Arch Linux: pacman
Debian(Kali Linux): apt-get, or aptitude
to install in your distribution type the above command just replace apt-get with your package installer.
From Source code:
Installing aircrack-ng from source code on any distribution is quite the same, because the code is written in C language and the C compiler on the system automatically compiles the code for the installed operating system.
Lets see how to install from source code,
Open Terminal and type:
Here, we changed the directory to Desktop. and downloaded the source code using wget command.
Extracted the downloaded tar.gz file using tar command
Why we are using sqlite=true is to add Airolib-ng support in the Aircrack-ng. We well see the use of Airolib-ng for Boosting WPA2 cracking speed in upcoming chapters.
For installing on Mac OS X you can click here
Now lets start using the aircrack-ng suite of tools
1. Make sure your wireless card is connected. Then open Terminal.
2. Type ifconfig and check your wireless interface, wlan3 in my case and we will be using wlan3 in the tutorial
If you type iwconfig wlan3 you should get something like this:
You can see Mode:Managed, now
What is managed mode ?

By default our wireless card works on Managed mode i.e it will only accept the traffic from the Access point it is associated(connected) to.
And for Wireless sniffing our card has to be in monitor mode so that it can receive traffic from any Wireless network without associating with it.
Here comes the first tool of Aircrack-ng suite of tools.
Airmon-ng
This tools is used to put the wireless card from Managed to Monitor mode and Vice-versa. Lets see how to put wireless card into monitor mode.
Put card into Monitor mode:
It will create an interface with name mon0, check using ifconfig.
Put card into Managed mode:
Here mon0 can be replaced by mon1, mon2, etc if multiple monitor interfaces are running..
Now we need to start sniffing the air. It can be done using
Airodump-ng
Airodump-ng allows us to
- Sniff the air using mon0 interface
- Dumping the captured packets into a “.cap” file, and
- Lots of INFORMATION !!!
Lets start airodump-ng
This is the basic command to run airodump-ng on mon0 interface.
It will show an out put screen like this:
We will cover the important information from the above output.
Line 1:
CH 4: Channel on which our card is currently scanning.
NOTE: As Wireless card is a type of radio, it can work on one channel at a time. You will see the Channel no. changing very frequently, this is called Time Division Multiplexing.
others are time elapsed and current Date-Time.
Line 3:
BSSID(Basic Service Set IDentifier) : MAC address of the Access point.
PWR: Signal strength of the incoming network, SI unit is dBm, greater the value in negative, weaker the signal strength.
ENC: Encryption type. can be Open, WEP, WPA/WPA2
ESSID: Access point name
Line 10:
Station: Client that is associated with the corresponding BSSID
Probe: Request sent by the Client for the Access point it was previously connected to. “rootsh3ll” in this case, see Line 13.
Press CTRL-C to stop scanning.
Data packets can be captured and saved into file using -w option with airodump-ng. Example
Press ^C to quit and Type ls test_data_capture*
Here airodump-ng has saved the output in .cap, .csv and .netxml format for different use.
We will use .cap file for our cracking process in this series.
Above steps has to be followed in every Pentest we will do. We will see the use of remaining tools
- Airbase-ng
- Aireplay-ng
- Airolib-ng
- Aircrack-ng
in upcoming chapters accordingly.
Conclusion
We learned to install aircrack-ng on Linux and windows systems. Putting wireless card on monitor mode and scanning the air and saving the information to a file for future use. as it will be used in WEP and WPA/WPA2 cracking.
Useful Links:
Router:
Network Adapters:
Alfa AWUSO36NH High Gain B/G/N USB / Alfa AWUS036NHA B/G/N USB
High Gain Antenna:

USB Drive (32 GB):
SanDisk Ultra Fit USB 3.0 32GB Pen Drive (International)
SanDisk Ultra USB 3.0 32 GB Pen Drive (India Only)

Any question ? Let me know, I will be glad to know and answer all your queries in the comments.
Don’t forget to share the post with all of your friends!
Aircrack-ng is a whole suite of tools for Wireless Security Auditing. It can be used to monitor, test, crack or attack Wireless Security Protocols like WEP, WPA, WPA2. Aircrack-ng is command line based and is available for Windows and Mac OS and other Unix based Operating systems. Aircrack-ng suite contains a lot of tools used for various purposes but here we’ll only look at some important tools that are used more often in Wireless Security testing.Airmon-ng
Airmon-ng is used to manage wireless card modes and to kill unnecessary processes while using aircrack-ng. To sniff a wireless connection, you need to change your wireless card from managed mode to monitor mode and airmon-ng is used for that purpose.
Airodump-ng
Airodump-ng is a wireless sniffer that can capture wireless data from one or more wireless Access Points. It is used to analyze nearby Access Points and to capture handshakes.
Aireplay-ng
Aireplay-ng is used for replay attacks and as packet injector. It can be de-authenticate users from their APs to capture handshakes.
Airdecap-ng
Airdecap-ng is used to decrypt encrypted WEP, WPA/WPA2 wireless packets with known key.
Aircrack-ng
Aircrack-ng is used to attack WPA/WEP wireless protocols in order to find the key.
Aircrack-ng is easy to install in Ubuntu using APT. Just type the following command and this will install all tools available in Aircrack-ng suite.
sudoapt-get install-y aircrack-ng
Usage
In this article, we’ll take a quick look at how to use aircrack-ng to crack an encrypted wireless network (TR1CKST3R in this example) to find the password.
First of all, list out all available wireless cards connected to your PC using ‘iwconfig’ command.
We’ll use ‘wlxc83a35cb4546’ named wireless card for this tutorial (This might be different in your case). Now, kill all the processes running on wireless card using airmon-ng.
Start Monitor mode on ‘wlxc83a35cb4546’ by typing
ubuntu@ubuntu:~$ sudo airmon-ng start wlxc83a35cb4546
Now, airmon-ng has started Monitor mode on wireless card, it’ll appear as different name ‘wlan0mon’. Run ‘iwconfig’ again to list wireless details.
Then, use airodump-ng to see nearby Wireless Access Points and their properties.
You can narrow down search using MAC (–bssid) and channel (-c) filters. To capture handshake (Handshake contains encrypted password), we need to save our packets somewhere using “–write” option. Type,
-c11 wlan0mon --write/tmp/handshake.cap
--bssid : Access Point’s MAC Address
-c : Access Point’s channel [1-13]
--write : Stores captured packets at a defined location
Now, we need to de-authenticate every device from this Access Point using Aireplay-ng utility. Write
-a : Specify Access Points MAC for Aireplay-ng
-0 : Specify number of deauth packets to send
After a while, all devices will be disconnected from that Access Point, when they’ll try to reconnect, running airodump-ng will capture the handshake. It’ll appear at the top of running airodump-ng.
Handshake is stored in ‘/tmp/’ directory, and contains encrypted password that can be brute forced offline using a dictionary. To crack the password, we’ll be using Aircrack-ng. Type
/usr/share/wordlists/rockyou.txt
-w : Specify the dictionary location
Aircrack-ng will go through the list of passwords, and if found, it’ll display the password used as key.
In this case, aircrack-ng found the password used ‘123456789’.
Now, stop Monitor mode on wireless card and restart the network-manager.
ubuntu@ubuntu:~$ sudo service network-manager restart
Aircrack Mac
Conclusion
Aircrack For Mac Os X
Aircrack-ng can be used to audit Wireless Security or to crack forgotten passwords. There are some other similar tools available for this purpose like Kismet but aircrack-ng is better known for good support, versatility and having wide range of tools. It has easy to use Command line interface which can easily be automated using any scripting language like Python.
